SOC for Service Organizations are internal control reports on the services provided by a service organization providing valuable information that users need to assess and address the risks associated with an outsourced service. The Trust Criteria for SoC2 are Security, Availability, Processing Integrity, Confidentiality and Privacy.
SECURITY
An auditor looks at IT security tools like WAF (web application firewalls), encryption and intrusion detection in addition to administrative controls such as background checks and authorizations. Access controls must adequately resist attempts at intrusion, devices.
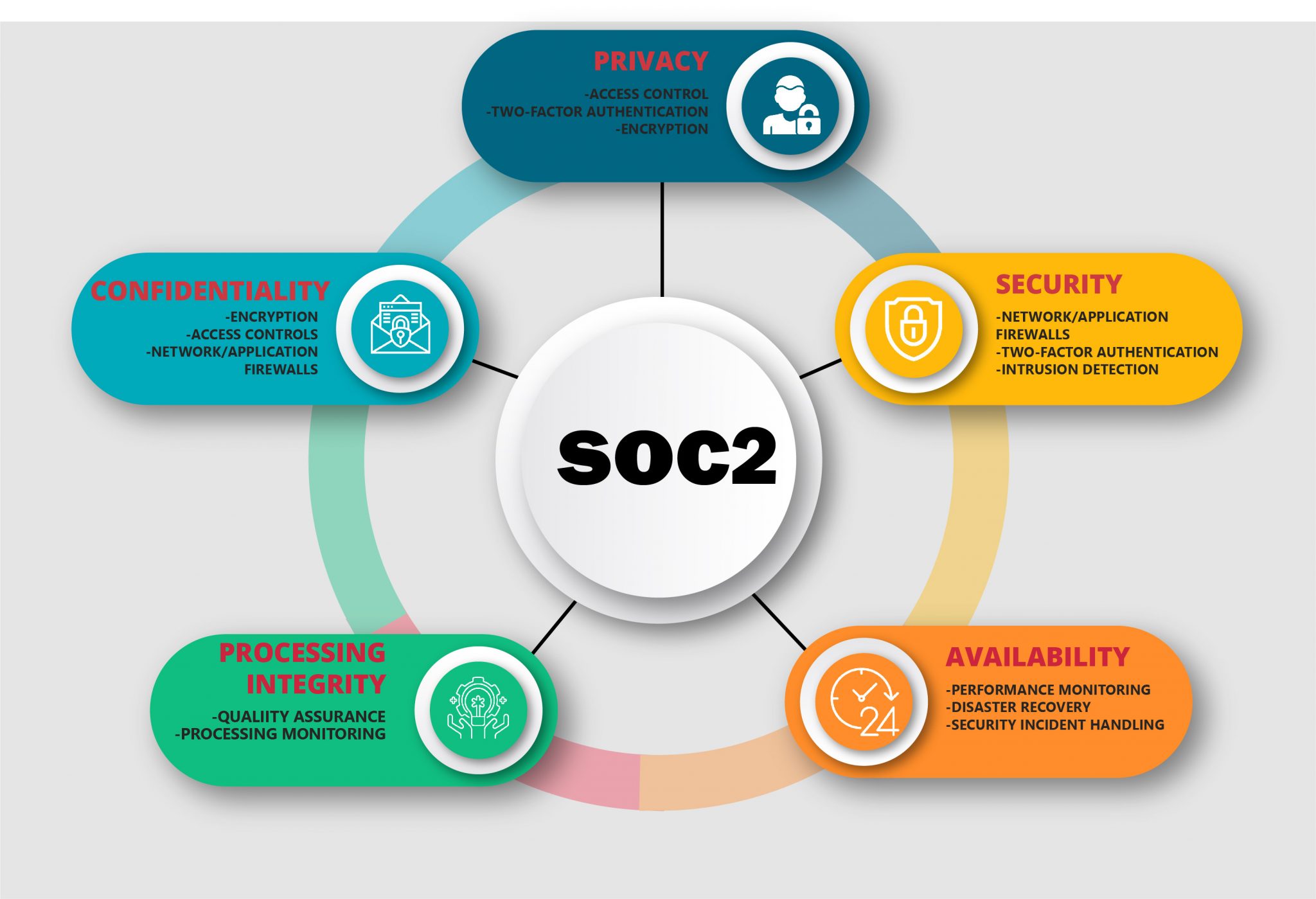
AVAILABILITY
The process, product, or service must remain available per the agreement between user and provider. To audit availability, an auditor must consider the reliability and quality of the network, response to security incidents and site failover.
INTEGRITY OF STORAGE
This principle is concerned with the delivery of the right data at the right time and at the right price— in other words, whether or not the platform performs as expected. Data processing must be complete, licensed, reliable and timely.
PRIVACY
The principle of privacy applies to the collection, disclosure, disposal, storage and use of personal information with regard to the generally accepted principles of privacy (GAPP) as established by the AICPA. It applies to Personal Identifiable Information (PII) including but not limited to names, addresses, phone numbers and social security numbers.
CONFIDENTIALITY
An auditor will take into account data encryption, network firewalls, software and access controls. If access to the data is limited to certain individuals or organizations, it must be treated as confidential e.g., business plans, internal price lists, intellectual property and other forms of financial information etc

